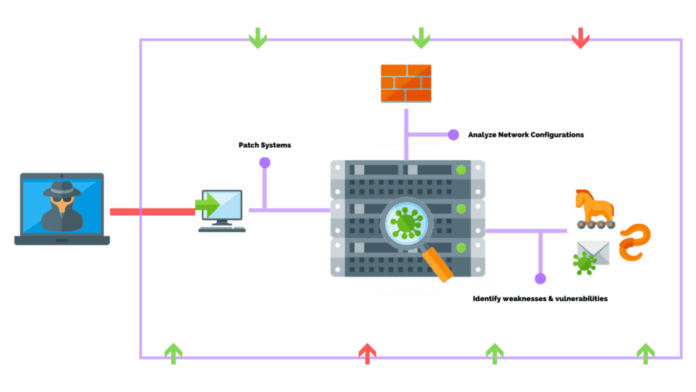
If you are a startup, a growing company or a successful giant in your field, you will need to periodically conduct network pentesting anyway. Safety is the foundation of a great reputation. Moreover, in some niches, it is impossible to obtain a license without meeting strict criteria. These areas include medicine, fintech, construction.
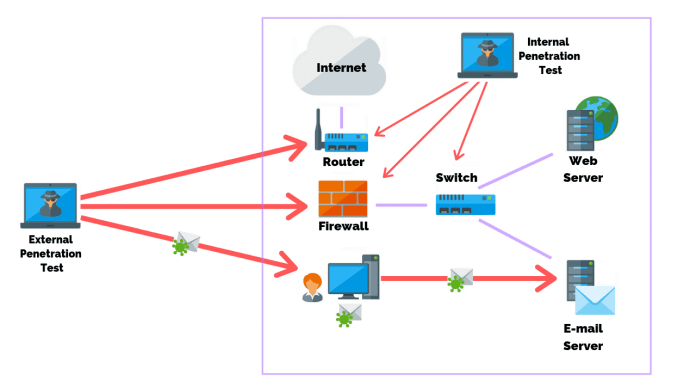
What needs to be done so that the research results are reliable and help to identify and correct critical points? You definitely need to find a professional penetration testing company. Read more here.
For these purposes, an ordinary IT team that is developing websites is not suitable. You need professionals who have experience in network penetration testing. It is desirable that the portfolio contains examples of work with businesses of different sizes and scale of automation. The more experience the testers have, the more they feel up to retrieve problems in the software or mobile application. It is also important that testers come up with a plan to address the deficiencies in parallel. Occasions when outsourced testers act with the client’s security team are encouraged.
What Is A Network Penetration Test?
This test is an endeavor to penetrate the customer’s network. This process is carried out applying various schemes and tackles. Thus, the client obtains the opportunity to see the vulnerabilities of the chain and correct code infelicities. The penetration test allows you to identify non-critical network problems, such as not responding to some variations of requests. This kind of testing simulates sundry nature of real hacker attacks.
What Are the Advantages of Performing A Network Penetration Test?

If a dedicated crew of experienced testers performs a series of penetration tests, the client will receive:
- Complete understanding of standard network behavior and settings;
- Security audit (including the ability of the security department to resist a hacker attack in real time);
- A set of methods to prevent data leakage.
It was customary to think that it only had sense to perform a penetration test for enterprises that were confident in their security system. This allowed getting a second opinion from the outside. Modern experts are inclined to believe that every company working with customer data or on the Internet should conduct a whole cycle of penetration tests. The first test needs to be done while still a startup. Then, when adding new services or expanding the business, the test must be repeated. Large companies are also encouraged to conduct routine preventive testing. Each test allows:
- Understand the basic level of the network by scanning ports and network devices.
- Check the current state of the security system and means of control over the situation (the testers managed to hack the system or not, if so, how long it took).
- Prevent data leaks from the local network by adjusting the protection strategy.
It is not uncommon for the security of a system to be compromised due to a one-sided defense strategy. For example, the company’s management developed a powerful external system, but did not think about internal hacking. It often happens that it is an intrusion from trusted hosts that turns out to be a successful way to steal data or spoof information.
What Are the Steps in The Network Penetration Testing Process?
Typically, a complete test cycle includes an overall vulnerability assessment. Then a planned hacker attack is carried out. The standard check includes 4 steps. The first step is to collect complete records about the application. It is also necessary to examine the client’s expectations. Already in the act of discussing the targets of testing with the customer, specialists begin to develop a scenario for carrying out three testing methods:
- Black Box Testing;
- Gray Box Testing;
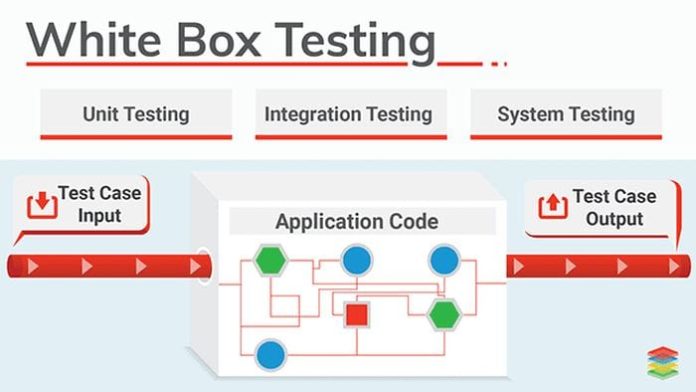
- White Box Testing.
The first option is an imitation of the actions of a typical hacker who acts from the outside. It is assumed that the intruder does not know how the system works from the inside. He also does not have access to the accounts of registered users or employees. This type of testing usually takes less time compared to other types. If the alleged hacker failed to break into external protection, this does not mean that there are no vulnerabilities in internal resources either.
Gray Box Testing is performed on behalf of a hacker who has some privileges in the system. For example, it may be an employee who does not have the most complete entrance degree. The tester can use a compromised account or a trusted host. This class of testing identifies both outside and inside security gaps.
White Box Testing models an assault from a position where the hacker has direct admittance to the software code or architecture. This trial is frequently the longest. It is not the experiment itself that takes the most time, but preliminary preparation. Third-party testers should review all technical security documentation.
Discussing customer expectations
The contractor must select the kind of testing (or conduct all three types in sequence) together with the business owner. It is necessary to stipulate the following conditions:
- Date, time and duration of the study;
- Carrying out an experiment in a trial encirclement or in live operation of the app;
- The need only to identify security discontinuities or the need to address them.
Reconnaissance and Discovery
After the specialists have collected the necessary records, the preparation stage is considered accomplished. The incoming stage can be roughly divided into two parts.
Reconnaissance
This part of the study helps to analyze the situation in real time. The tester manually (or automatically) collects data about the system that needs to be hacked. An initial scan detects the presence of all ports, devices and systems. Also at this stage, the tester identifies a list of theoretical weaknesses. The selection is based on the experience of a specialist. Then the tester starts checking each security loophole in turn. Successful tactics used at this stage include:
- Social engineering;
- Mental traps for employees in order to disclose confidential information.
Discovery
This stage accumulates all the actions of the hacker when he found the desired gaps. Each open port or hacked account of the system is checked for the possibility not only to penetrate the system, but also to download data from there.

Direct Penetration Testing
In this step, the technician checks in real time every opportunity that he discovered in the previous step. At the beginning, the tester works out the scenario that he considers the most simple. Next, less vulnerable points are tested. Be sure to record the time that the tester spent hacking the network. The strengths of the security system are also recorded during the exercise.
Technical Approach
This part of the work is aimed at breaking the system by using holes in technical protection. For example, a tester found that the client base could be accessed through port X. This port also has internet access. The attack is carried out by overflowing the memory buffer and while the system is reacting, they try to download records or make changes.
Human Approach
If the previous method did not give results, social engineering is applied. The most popular method is using phishing attacks. Key employees (managers, employees of the finance department) are sent emails with malware. Employees are searched for personal data on social networks. As soon as the employee opens the letter and follows the link, the malicious program is automatically installed on the computer and begins to collect private information.
Reporting, recommendations and corrections
A business owner gets more than just a list of software security vulnerabilities. The testing company should propose a list of remedies for any identified problems. The report provides a detailed description of the testing act, its type, initial data, time spent and opportunities for improving app protection. An IT company can offer a number of technical measures. But experts also often give recommendations for improving the overall security policy. It necessarily includes rules and instructions for employees.