The cloud has the potential to be safer than on-premise data storage, but it requires some intentionality and effort on your behalf. If you want to maximize the innate security features that the cloud offers, you must pay attention to the details.
The Challenge With Cloud Security

One of the major selling points of the cloud, particularly as it pertains to data storage, is that it’s more secure than on-premise solutions. And while this is true, it doesn’t mean cloud storage is without its own issues, concerns, and risks. As hackers become more familiar with the cloud, they’re finding new ways to exploit it. And it’s up to businesses to respond in an appropriate manner.
According to CheckPoint Software, a leader in cyber security solutions, there are seven major cloud security challenges:
- Increased attack surface. The problem with the public cloud is that it’s become extremely large. And as it’s grown, it’s become a more attractive attack surface for hackers who are looking for easy opportunities to exploit poorly protected entry points. Everything from Malware to Account Takeover have become fairly standard threats in today’s cyber landscape.
- Lack of visibility and tracking. Whether it’s an Iaas, SaaS, or Paas cloud model, the cloud provider typically has total control over the infrastructure layer. This means a lack of visibility and control from the user side – making it difficult to identify and quantify cloud assets.
- Ever-changing workloads. The dynamic nature of cloud platforms allows assets to be provisioned and decommissioned automatically – at both velocity and scale. This is what makes these platforms so efficient. However, it also creates challenges for off-the-shelf security tools that aren’t flexible enough to adapt.
- DevOps, DevSecOps, and automation. For organizations that choose to embrace DevOps, it’s imperative that security controls are identified and embedded in code as early as possible in the development cycle. Any security changes that happen to be implemented after the workload has been deployed can actually undermine the organization’s defenses and create issues.
- Granular privilege and key management. This is a major issue that often goes undetected. It occurs when cloud user roles are configured without much strategy and extensive privileges are given beyond what’s required. (e.g. Giving an untrained user database delete or write permissions when they have no need to do either.) Not only does this expose the organization to insider threats (human error or malicious activity), but it also gives outside hackers more ingress ports to access data.
- Complex environments. As cloud solutions advance and businesses find themselves staring down such a wide array of technology, it can be difficult to know exactly how to proceed. Some businesses suffer paralysis by analysis, while others implement so many different approaches that they lose clarity.
- Cloud compliance and governance. Every business is responsible for making sure that their data processes and workloads are compliant. Unfortunately, many lack the tools required to conduct compliance audit processes or obtain real-time alerts about misconfigurations.
How you address these seven challenges will, to a large extent, determine how secure your business is moving forward. A failure to acknowledge their existence leaves you prone to compromising attacks, whereas a strong emphasis on advanced security principles will strengthen your perimeter and allow you to focus on growing your business without fear of external threats.
5 Ways to Improve Cloud Security

Left unattended, it’s pretty clear that your business is vulnerable to external threats and hacks. But that doesn’t have to be your story. With some fairly simple techniques, strategies, and investments, you can improve your cloud security and enjoy much greater peace of mind.
Here are areas to focus on:
1. Password Security

We often picture hackers sitting in some complex underground server room, deploying advanced software and revolutionary tactics to hack into a cloud system and steal a company’s sensitive data. But this isn’t always true.
The reality is that most hackers still prefer to infiltrate the good old fashioned way: By compromising a user’s login credentials. And this is why password security is more important than ever.
If you want to protect your business, you need to practice better password hygiene. This means implementing complex passwords that are changed regularly and used only once. It also means disabling automatic logins and not storing passwords where they can be easily compromised or stolen (like on a desktop or sticky note).
2. Multi-Factor Authentication
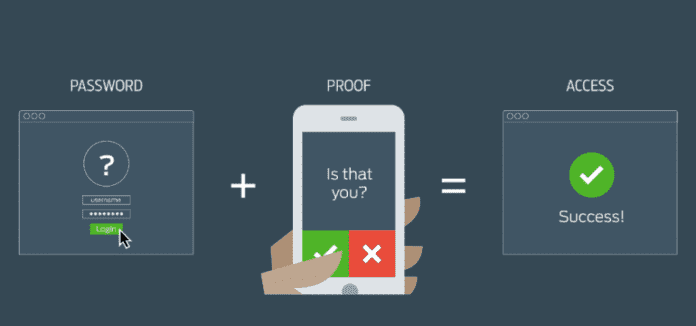
In addition to having robust passwords that are rotating out on a regular basis, you also need multi-factor authentication. Whether it’s two- or three-factor authentication is up to you, but each additional layer you mix into the equation dramatically reduces your odds of being hacked.
3. Updates
It’s absolutely imperative that you keep your platform updated. Enabling automatic updates is definitely the best option. However, if you choose to do them manually, it’s wise to set up some sort of notification system so that you never fall behind.
4. Encryption
Data should be encrypted at every step of the process – including at the source and in transit. This is the fastest and most secure way to protect your data.
Encryption helps ensure you’re complying with all contractual obligations and industry regulations (in regards to how you handle sensitive data). But it’s wise to go beyond the base level requirements. Encryption standards will likely become even more strict in the near future and it’s helpful if you already have the proper measure in place.
5. Vulnerability Testing
Regardless of which cloud server provider you use, they should have some sort of incident and vulnerability response tools included. Ensure that these tools support automatic security assessments so that you can test the weakness of the system at all times. This limits the amount of time between important security audits and allows you to perform scans automatically or on demand.
Position Your Business for Success

Where is your business on the cloud security spectrum?
Are you proceeding with a blindfold mentality and hoping that nothing bad happens? Or are you proactively investing in advanced cloud security solutions and safeguards that keep you out of harm’s way?
Most businesses fall somewhere in the middle…and that’s okay. But now is the time to reevaluate where you are and address underlying vulnerabilities so that you can limit risk and have peace of mind.









